Category: Technology
Aug 03, 2021 Technology
Things You May Not Know About Managed Cloud Rendering Services
Staying aware of the specialized side of business these days is a test that many organization proprietors are not well ready for. Advertising can be an interesting undertaking on the off chance that you are not state-of-the-art on the latest innovative advances in contacting crowds and clients, everything being equal. With the advancement of the Internet readily available, there are open freedoms for organizations to publicize and advance their administrations. Shockingly, numerous organizations miss the mark since they do not have the capacity or methodology to put forth sure their attempts pay off and end up imploding under the tension of the serious market. Moreover, security breaks can be exorbitant and hard to fix without the legitimate labor information and ability. It is significant that entrepreneurs become more acquainted with the administrations out there that have as of late been created to address these ordinary issues that organizations face around the world. Perhaps the most accommodating advancements is the inception of oversaw cloud administrations. Cloud administrations have gotten a norm for some organizations to store and access their information and friend’s data out of nowhere, from some random area. Here are some different things you may not think about oversaw cloud administrations.

It is not just about capacity and openness
First and foremost, cloud administrations do not simply deal with the capacity and openness of organization data. They additionally offer different administrations for example, providing organizations with programming by means of the web that are customized to that particular organization’s necessities and why not find out more megarender.com. There are perfect and clean installment choices that accompany cloud administrations; at times it depends on a level rate, different occasions it depends on the product and administrations that you use most. You ought to make certain to investigate whatever you will utilize the most and how the organization charges for the administrations. Moreover, entrepreneurs do not need to stress over refreshing their product consistently or keeping steady over business security; cloud benefits regularly update and develop your security by sponsorship your data consistently without need for your brief or inclusion.
Organization information is ubiquitous
Something second you may not think about oversaw cloud is that organization workers can team up and counsel from any area. You can connect the organization information to any representative’s specialized gadgets and it regularly synchronizes the data all alone so you do not need to stress over saving archives, it essentially does it for you with every amendment or alteration. Sharing postulations capacities progressively is quite possibly the most fantastic advancements in innovation lately and organizations are exploiting the advantages. For example, representatives the nation over do not should be flown in for conferences, going over spread sheets or making changes to field-tested strategies they can basically all adjust and view a similar record simultaneously.
Aug 02, 2021 Technology
What Do You Know About It Security And Cyber Security Singapore?
People always have a fear of getting their details leaked online. And we call it a cyber attack. However, most of the time, it is taken as a grave issue when many people have faced the same. In many ways, the IT security and cybersecurity Singaporedepartment is trying to solve the issues.
So don’t you ever felt like that you should know about how it works? Though as a non-technical person, there is nothing that exists which you can’t be understood. And that is why you need to read this article to know about it security and cyber security singapore. Since then, only the efforts those people take to get the actual weightage. Yes, in other ways, we can say that a collective effort can make things get better even if it was a hard one.
The Services Offered
You will also need the service from cybersecurity in certain manners since people are sitting out there to hack the data and sell it somewhere as a fraudster. So to be safeguarded from those, you need highly intelligent services to make sure that your company and you are protected from cyber-attacks.

So now is the time to get to know about the services offered by IT security and cybersecurity. They are:
- Audit services
- Advisory services
- Security testing
If you haven’t heard about these services, then you can read a brief about them here. The auditory services are needed when you have to ensure that company’s data is secured every major time. For that, you need a special service called audit from these security departments to assure. When it comes to advisory ones, just like the name of the service, they provide you pieces of advice. There are many instances you will be facing issues and are waiting for someone to help. And also, the security testing is almost the same as audit ones. The common intention of every service here is security and protection assurance.
Jul 23, 2021 Technology
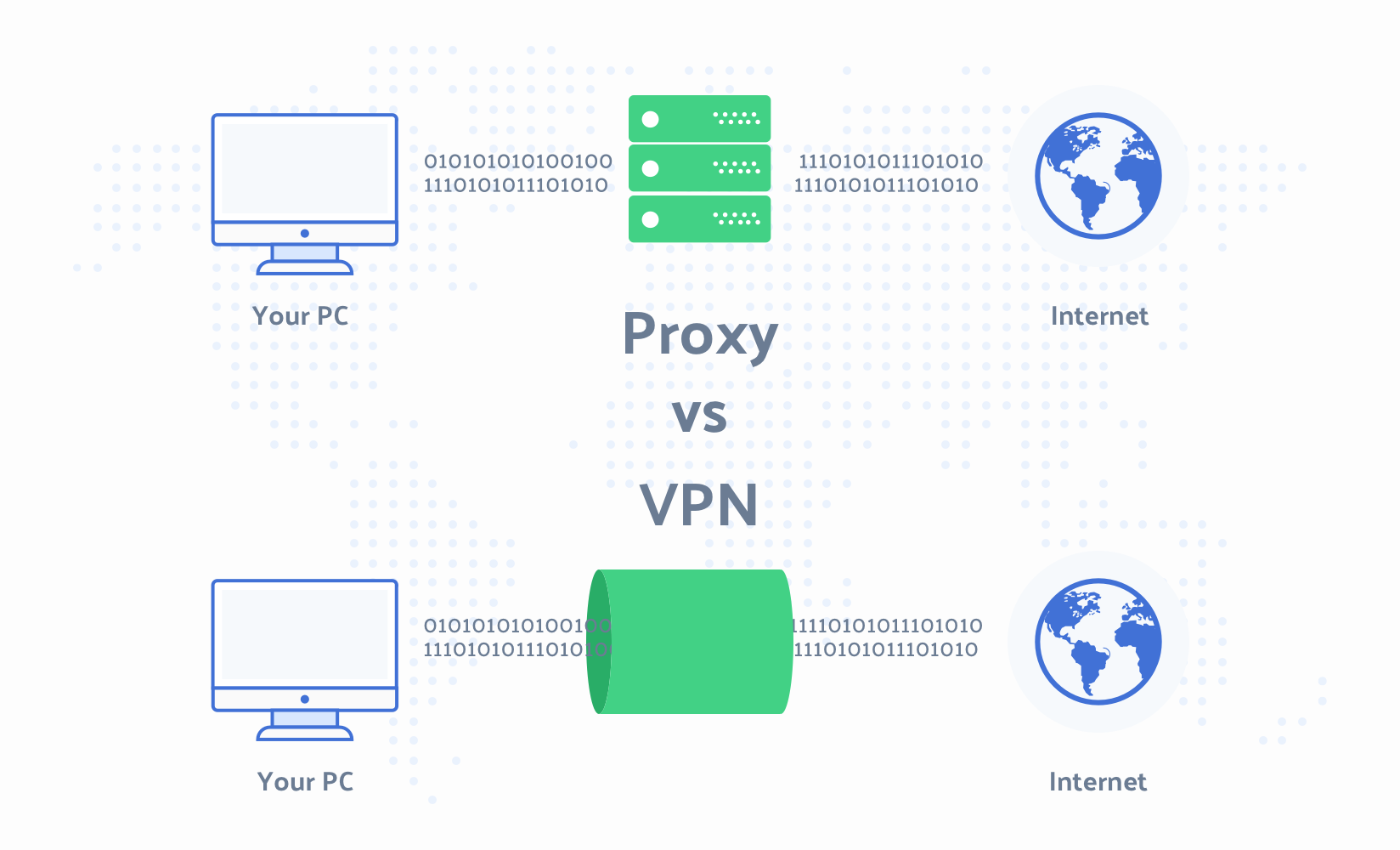
Use a Proxy Server to Stay Anonymous – An Interface Phenomenon
You can utilize an intermediary worker to remain mysterious on the PC organization. It implies that the intermediary worker that you use would not uncover your unique IP Internet Protocol address. Through an intermediary worker, the customer connects with different administrations present on the organization. The client interfaces with the worker and afterward the worker demands for a specific page or record present on the organization. Notwithstanding, it is not prescribed to utilize an intermediary as different PCs on the organization associate with your framework through IP address as it were.
Be that as it may, in cases, where you need to conceal your character and need to save your framework from any sort of programmer assault, an intermediary worker can be utilized. There are number of ways by which intermediary can be accomplished to remain unknown on the organization. While utilizing a site intermediary worker, you enter the URL that you need to visit in the space gave on the intermediary site and look at here now https://you-proxy.com/. The intermediary site sends the solicitation for the page further to the source worker and afterward shows back the outcomes to your screen. This kind of worker does not recognize itself as intermediary worker and your IP address is not uncovered too. Site intermediary workers can channel the data showed on the page by which the unseemly substance like advertisements, java-scripts and so forth do not run on the site page.

A few workers may accompany a sticker price while others might be thoroughly liberated from cost. You can discover them in the net. You can undoubtedly shroud your IP address utilizing this kind of worker. You can likewise utilize Anonymizer to stay unknown on the organization. Typically, these are paid administrations and the greater part of them has their own interface that permits you to shroud you IP address. You can utilize certain product programs that conceal your IP address. These projects arrange just as deal with your setting so you can become unknown. By utilizing these product programs, you can undoubtedly sidestep certain settings in the event that in the event that you do not have a lot of information about intermediaries.
Treat Technology can likewise be executed to conceal your IP address. You can undoubtedly impair treats by utilizing the program alternative. Thusly, sites cannot save information on your PC. This can give a specific degree of secrecy to the client. For all out secrecy on the organization, socks innovation can be utilized by the customer. Socks conventions are utilized in this innovation in which a socks worker demands just as retargets the information that is sent back. It becomes difficult to figure the customer’s IP address as uncommon socks conventions are executed. There are specific kinds of intermediary workers particularly straightforward, contorting and high secrecy intermediary workers that can be utilized to conceal your IP address.
May 02, 2021 Technology
Need of Control Flow Obfuscation in Coding Languages
Windows Control Flow Obfuscation is necessary if you have found this odd, new malware installed on your computer. This imitation, rogue spyware software was made by the exact cyber-criminals who fabricated the bogus Microsoft Security Essentials virus. Therefore, it is easy to be duped by this official-looking software that conveys all the Microsoft logos and recognizable graphics. But this is dangerous spyware. It may harvest your personal information, steal money from you, and put you in danger of identity theft. You have got to remove Windows Debug System as soon as possible.
This virus will display Warnings of an unknown Win32 and Trojan issue on your computer. You will be bombarded with pop-ups, browser redirects, warning drives, and alarms. Here is an example of an error message that you will encounter:
If you allow these messages trick you, then your PC will be controlled by this virus. You would not be able to uninstall Windows control flow obfuscation via an avenue like Add and Remove programs, and each time your computer boots up, the imitation scan will run. Most often, the purpose to blame is some tiny bit of code that somebody wrote but believed so trivial that he believed it did not require testing. In addition, the function to blame is often relied upon by many other functions of this program
Your PC becomes slower, your normal programs no more available, your folders become corrupt, and worst of all, your privacy is compromised because of the harvesting nature of viruses like these. You cannot allow your personal data and financial information be moved to cyber criminals. You have to do away with Windows Debug System to protect what’s important you.

Getting rid of the virus can be done manually or mechanically. The manual process is only suggested for those users that are comfortable editing the registry of their PC. This is only suggested for the most advanced users, due to the cautious nature of registry editing. A single error can end up costing you hundreds in IT repair fees. Having said this, to correct the issue manually you will have to locate the registry values associated with the virus on your HKEY_CURRENT_USER folder and then remove them. Then you will have to eliminate related DLL and LNK files left behind when the app installed itself. Then you are going to delete the folders and files associated with the application, and eventually stop the procedures connected with the application in your task manager. A complete list can be found on my website, and please make sure to back up important files before you try to edit your registry.
Feb 16, 2021 Technology
What Are RSocks Proxy Servers and What Are They Used For?
There are numerous approaches to remain mysterious on the web however perhaps the most widely recognized is by utilizing what are called proxy servers. A proxy server is a machine that acknowledges approaching web demands and afterward advances them onto the objective; they resemble the center men of the web and keep your PC and objective web server independent.
What this fundamentally implies is that when the 4g proxy server gets your solicitation it looks like it has come from the proxy server, accordingly taking everything into account you actually have not visited the site. There are various sorts of proxies yet the primary ones are:
HTTP Proxies – These are utilized for HTTP traffic and would be significant for the above model.
Sifting Proxies – These are generally found at work and are utilized to hinder admittance to specific sites and to forestall data transmission squandering; these are not utilized for protection.
SOCKS Proxies – These are utilized to burrow different sorts of traffic which could incorporate courier or ftp traffic.
Proxies can likewise be arranged into one of the underneath:
Unknown – These do not distinguish you to the end server and accordingly keep you mysterious. They can be separated into two other sub classes – tip top and masked. A tip top would not separate itself as a proxy server to the end machine. A hidden then again will give up sufficient data for the end machine to acknowledge it is a proxy server, anyway it would not give out your IP address and in this manner your security is unblemished.
Regarding security there are some different contemplations to make. Initially there are various spots to get your proxies from. You can get public ones which anyone can utilize or you can utilize private ones that will set you back. Except if you are 100% certain about the source that is facilitating the proxy you can never be too certain whether they are gathering logs and in the event that they are, well your protection is not so private all things considered!
This is the reason in the event that you need to have true serenity and appropriate security you ought to get your proxy servers from a respectable organization and guarantee that in their terms and conditions they express that they do not gather log records. Numerous not all that genuine organizations will reap their proxy server from botnet pervaded machines and albeit this will mean you do not need to stress over any logs being gathered, it likewise implies that you are financing a potential criminal organization online that represent considerable authority in bringing in cash from selling taints machines!
Jan 01, 2021 Technology
What Is Meant by Reverse Proxy Server?
A Reverse Proxy Server is the best arrangement that can be used in the event that you need to conceal the interior workers from your customers for security concerns. A converse worker can either be an electronic or an application that is introduced inside a similar organization as the inner web worker and further acts like a shield for the workers in the organization. At whatever point there is a solicitation to both of the web workers situated in the organization from the Internet, the solicitation needs to go through the opposite worker first, which either manages it without anyone else, or whenever required, sends it across to the next web workers. While sending it to the different inside web workers, the converse worker utilizes load-adding, accordingly addressing the requirements of inbound traffic to the worker s.

There are various advantages one can identify with this, as follows:
The converse intermediary workers are all around shielded from the pernicious web assaults including infections and malware, subsequently improving the strength of the interior organization.
At the point when the opposite worker is made to handle storing, the outstanding burden of the worker diminishes. This is the reason it is likewise known by the name of https://proxy-seller.com/sneakers-proxy.
Through opposite alternative, the SSL encryption is dealt with by the intermediary without any assistance.
The opposite worker encourages the appropriation of burden to different inward workers in the organization. This prompts expanded productivity and decrease in turnaround time.
If there should arise an occurrence of a major page being mentioned, the equivalent can be created and given to the opposite intermediary, who at that point coddles it to the customer, and the worker does not stall out during that period.
The reaction itself can be improved and packed by the converse Proxy Server before the equivalent is being passed to the customers. Actually I would not realize how to see if a trustworthy organization is running an intermediary worker or on the off chance that it was programmers, yet there is a generally excellent protection programming out available since will permit you to surf and purchase securely on the web. You will approach a huge organization of private intermediaries to utilize; the program itself is quick and totally scrambled, permitting you straightforward surfing. There is no better, it is the best available.
Sep 06, 2020 Technology
Top Persona Design and style Tips for Animation Videos
Figure design is not really that easy as it appearance in cartoons, videos and animated graphics. It will require long hours of developers to create a personality for the scenario. Figure planning could have difficulties, nevertheless the designers generally aim to keep them basic. It’s more than simply readable features, clear lines that are required inside a personality. It is additionally about where you should focus on and where to downplay based on the personality of the character inside the scenario. We certainly have observed Disneyland cartoons, Tom & Jerry, Ice-cubes Era movies, Jungle Guide and thus more, and every individuality in each of the afore mentioned made a solid affect in our thoughts to stay living forever. To start out building a character is quite challenging but when a single has the notion of the type inside the thoughts then tips below would be beneficial.
The crowd of the any artistic venture is important in identifying its platform. It should be the most important phase on the best way to creating heroes. The character types created for children are happier in colours and possess obtained very basic styles. If an individual is doing work for customers jobs then you need to go by the character requirements discussed by your buyer. Where placement and the way the type will probably be unveiled within the scenario also performs a vital role in character creating. In doing what medium sized persona will probably be viewed even offers a part to show right here. Usually tiny methods like cell phone do not need intricacies within the character types as the large display screens will need. Besides, whatever the method is, figure creating constantly starts with document, pen, plenty of sketches, suggestions and a lot more.
You should make an analysis of why some figures are effective and some usually are not. Perform a proper study and thru review of your different figures showing in cartoon stations, Animatievideo, ads, and so forth. Whether its form, its personality, its clothing or its colour, animation heroes should be unique to face in the competition. It could be an animal or possibly a individual or monster, the type patterns must be exciting to draw in the eye of people.
Jan 19, 2020 Technology
Going the Extra Mile through Fleet Management

While dealing with a fleet think about that you are utilizing the correct vehicles and that these are being overseen proficiently. Utilizing a vehicle fleet the executive’s administration can help with this administration yet what are the key advantages?
Picking the Right Kind of Vehicle
Utilizing the correct sort of vehicle for your business can majorly affect the amount you spend and the degree of administration you give. It is not only an instance of utilizing vans or vehicles; it could even be guaranteeing that you are utilizing the correct sort of vehicle. It does not seem like the primary thing you’d consider – normally accepting any respectable vehicle will do – however various models are better for various purposes. For example, your fleet may be about picture as much as it is about vehicle, so you will require a glory sort of vehicle. On the other hand, the facts might confirm that your organization cooks for long separation occupations and you would in this way need a low support vehicle with proficient fuel yield. To accomplish this, it is essential to remain side by side of any new models discharged into the market, something that a vehicle fleet the board administration can accomplish for you. They can likewise give a pool of vehicles from which to browse, including most significant producers.
Going the Extra Mile
Vehicle appraisal is a significant piece of any fleet the board administration as this assesses things like hazard and cost-adequacy route optimization software. Having an expert and experienced organization do this for you will guarantee that you are well-educated to settle on the best choices with respect to your fleet.
Fleet Management Software Helps Companies Boost Efficiency
Associations that work countless vehicles can profit by far reaching fleet the board programming. There are numerous components that can influence the effectiveness and efficiency of an organization’s vehicular resources and without the correct fleet upkeep programming, supervisors and entrepreneurs may think that it is hard to completely boost their fleet’s abilities. Highlights, for example, stock and buy request modules for programmed parts reordering can enormously improve these procedures, and guarantee the consistent accessibility of fundamental car parts. Actually, present day frameworks for dealing with a fleet of vehicles can follow work and material expenses on either a month to month or a yearly premise. Picking the best fleet the board programming is not a simple errand. While there are numerous that guarantee to offer highlights and instruments for better and progressively effective fleet support and the board, not all can really give what they have guaranteed. In any case, working with an arrangements supplier with a strong reputation of helping associations robotize fleet support and the board is a decent method to begin.